Database Locking Strategies
If no COMMITs are issued during the program locks arent released until the program completes thereby negatively affecting concurrency. See Section 8111 Internal Locking Methods.

Data Concurrency And Consistency
There are two types of locks that fall under the category of pessimistic locking.

Database locking strategies. Time stamp automatically generates. Changing the locking methods is best done via locking hints in the queries or by changing the ISOLATION LEVEL in general for the stored procedure or connection. This is the least restrictive level of locking.
Database scanning is the mechanism for deciding when records should be processed. Select for update - This holds an. This concurrency control strategy involves keeping an entity in a database locked the entire time it exists in the databases memory.
Record Locking In Database. A unique binary number every time you update the SQL Server data. This is done with the SET ISOLATION LEVEL command or by changing the isolation.
The shared lock on a database level is imposed to prevent dropping of the database or restoring a database backup over the database in use. Record Locking In Database. Locking mutual exclusion is done to prevent two different tasks from simultaneously modifying related database records.
Concurrency Control Locking Strategies. We recommend that you do not override the default locking levels which have page and row locking on unless table or index access patterns are well understood and consistent and there is a resource contention problem to solve. Using the SNAPSHOT Isolation Level will add a lot of load to the tempdb as your database load increases.
Programs using the repeatable read locking strategy hold their locks until a COMMIT is issued. Suppose the example as soon as A opens his account through his ATM card. There are three main approaches used each with its own advantages and disadvantages.
Solution number 2- Use timestamp data type. External locking occurs when the server and other programs lock MyISAM table files to coordinate among themselves which program can access the tables at which time. Describes Agile Modeling Driven Design AMDD and Test-Driven Design TDD approaches database refactoring database encapsulation strategies and tools that support evolutionary techniques Agile software developers often use object and relational database RDB technology together and as a result must overcome the impedance mismatch The author covers techniques for mapping objects to RDBs.
Locking protocols are used in database management systems as a means of concurrency control. The first three requests to the database the initial lock marking if appropriate the source data and unlocking can be performed as a single transaction. The SQL Server Database Engine uses a dynamic locking strategy that automatically chooses the best locking granularity for queries in most cases.
Shared locks read locks and exclusive locks write locks. The locks will be held until your transaction completes. There are other approaches to setting exclusive locks on rows and I want to understand the best practices for Oracle table locking.
The clinical monitors can be provided with sets of data to be addressed and once done the. There are generally two types of locks. Using Page-Level and Record-Level Locking Whereas opening a database in exclusive mode locks the entire database and recordset locking locks one or more individual tables page- or record-level locking locks only the page or record containing the record that is currently being edited.
This locking strategyprovides good consistency at the expense of throughput. Acquires locks on entries then and holds the locks until commit time. Write lock and read lock.
2 This limits or prevents users from altering the data entity that is locked. Record Locking mechanism is the most common method to implement the concurrency control in DBMS. Optimistic Locking is a strategy where you read a record take note of a version number other methods to do this involve dates timestamps or checksumshashes and check that the version hasnt changed before you write the record back.
This strategy is most applicable to high-volume systems and three-tier architectures where you do not necessarily maintain a connection to the database for your session. Best lock strategy to prevent deadlock on concurrent updatesHelpful. Hence we require a mechanism to manage the locking requests made by transactions.
When interacting with a relational database this is done by actively locking database rows or even database tables when you retrieve the data you will operate on. Please support me on Patreon. This can cause lock timeouts and lock escalation.
For example when a SELECT statement is issued to read some data a shared lock S will be imposed on the database level an intent shared lock IS will be imposed on the table and on the page level and a shared lock S on the row itself. The next two interactions to lock and obtain a copy of the source data can easily be combined as a single trip to the database. One way in which database lock can be smoothed is to create cohorts of data perhaps based on sets of subjects who were enrolled or randomized by a certain date.
Multiple transactions may request a lock on a data item simultaneously. Takes a before image of every record that the transaction touches and compares the image to thecurrent entry. Locking means record or set of records must be locked for other users when it is opened for update possibly by any user.
In this situation the client cannot actually maintain database locks as the connections are taken from a pool and you may not be using the same connection from one access to the next. The basics of record processing involves obtaining the current value of input fields and outputting the current value of output fields. The other way of doing optimistic locking is by using TimeStamp data type of SQL Server.
This type of locking is internal because it is performed entirely by the server and involves no other programs.

Everything I Know About Distributed Locks By Davide Cerbo Medium
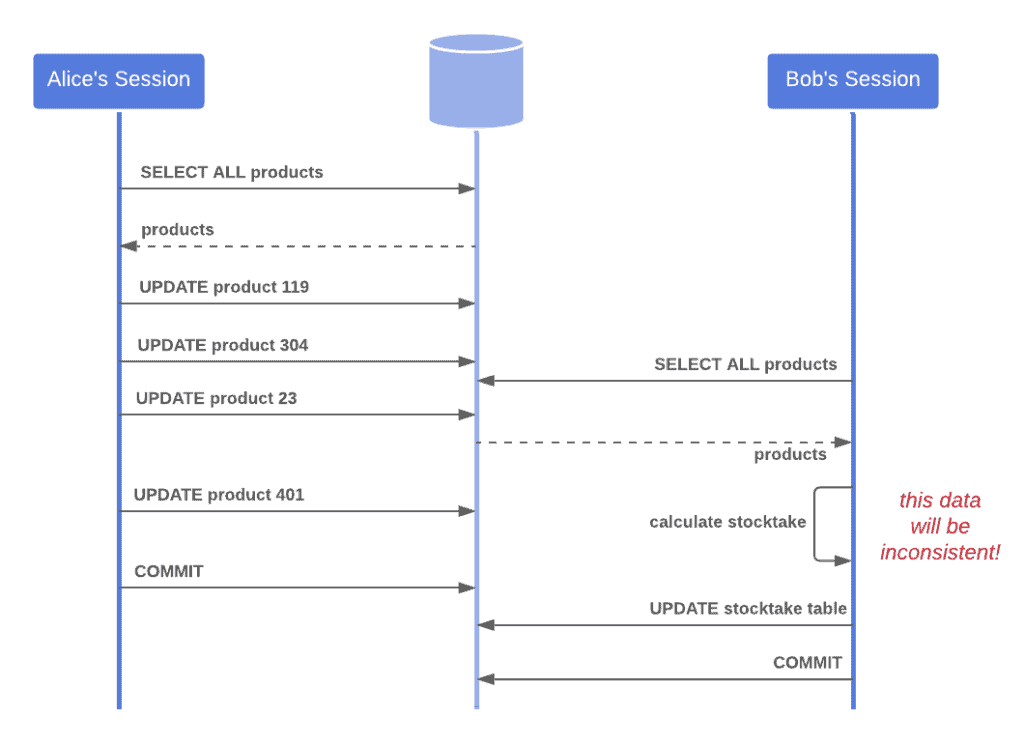
Offline Concurrency Control Baeldung On Computer Science
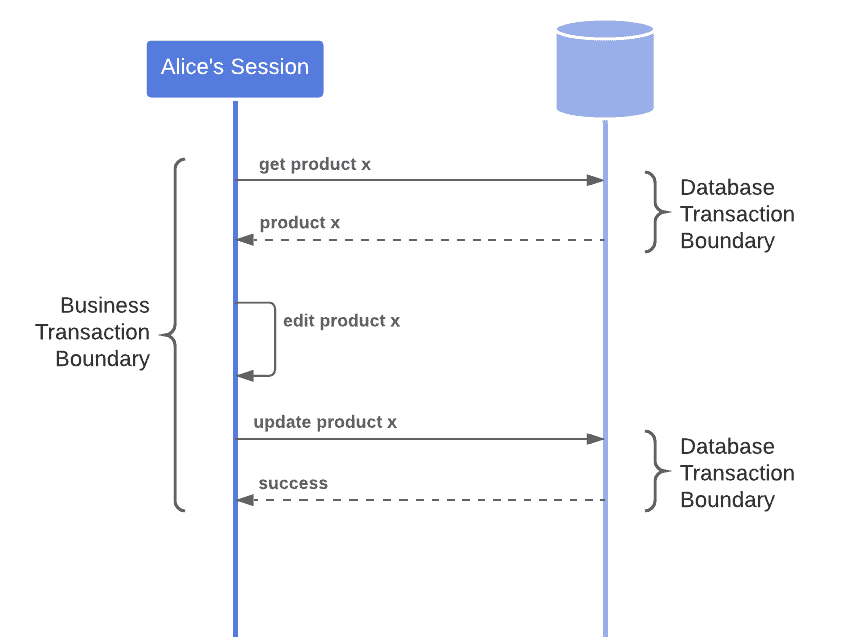
Offline Concurrency Control Baeldung On Computer Science
Introduction To Database Concurrency Control
Posting Komentar untuk "Database Locking Strategies"